You’ve considered the merits of cloud computing. You’ve made digital transformation part of your business strategy. And now you’re thinking about moving your on-premises servers and applications to the cloud. What’s next? It’s time for a comprehensive cloud readiness assessment to examine your business priorities and your technical infrastructure.
A cloud readiness assessment is an intensive evaluation of an organisation’s existing IT system that is designed to identify cloud-suitable and cloud-unsuitable resources. The assessment is usually conducted by cloud professionals in partnership with senior members of the organisation’s managerial and technical teams.
Executives are asked to share strategic insights about business priorities, objectives, and deliverables, while IT stakeholders are relied upon to provide holistic information about the system architecture and associated assets. Current and future business scenarios are discussed, with cloud consultants generally focusing on three key areas…
Businesses typically look to the cloud to reduce costs, increase operational efficiency, or improve security – but there’s often a specific trigger behind the actual decision to migrate.
Pressing capacity needs, compliance concerns, and expiring data-centre contracts are some of the common catalysts. At present, the looming end-of-support dates for Windows Server 2008 and 2008 R2, as well as SQL Server 2008 and 2008 R2, are prompting many companies to embrace cloud technology.
Cloud consultants aim to uncover the business’s main priorities so they can determine which cloud solutions are the most appropriate. Their goal is to facilitate a seamless migration process, but that’s only possible when they have a complete picture of what the business is hoping to achieve by moving to the cloud.
Depending on its size, the business may run hundreds or thousands of applications across a variety of servers. How are these applications structured? Can they be modified for the cloud? What technologies are being used? How are they organised?
Consultants need to create a thorough catalogue of the business’s on-premises applications and servers, with explicit particulars about architecture, communication, and dependencies. This inventory is especially important for determining whether applications should be rehosted, refactored, rebuilt, or replaced in the cloud.
It’s also vital for cloud specialists to understand how the business’s resources are currently being used. What’s the status quo, in terms of app volume and usage? What are the system requirements during normal operating conditions? And during peak periods?
Cloud consultants must have a clear idea of the resources that exist in the business’s present environment, what they’re being used for, and where they belong in the system, so that migration teams can create appropriate guidelines for moving servers and application stacks.
How does the business handle data? Where is data processed and stored? What data-specific industry rules and compliance regulations apply to the business? Consultants have to explore these questions with relevant stakeholders during the cloud readiness assessment.
Data privacy and data security are core concerns for all South African businesses that manage sensitive in-house material and confidential customer information. Foreign decrees like the European Union’s General Data Protection Regulation have the potential to affect local entities. And SA laws, including the Protection of Personal Information Act, dictate the relationship between businesses and consumers. Legal obligations and compliance considerations must be reviewed during the readiness assessment.
A successful cloud migration requires extensive preparation and careful planning. The readiness assessment is the first (and most important) step. In our next article, we’ll take a closer look at Step 2: The Road Map to get to grips with the blueprints for cloud migration. In the meanwhile, learn more about app migration to Microsoft Azure by watching these videos…
Artificial intelligence will allow companies to stay competitive by utilising key technology to maximise user interaction. Check out the infographic below to see how edge devices can extend power across multiple platforms and environment.

At our recent Intelligent Cloud Security Conference in Cape Town, Technical Director Willem Malan pointed out that around 90% of South African corporates are already using the cloud in one way or another. “The main takeaway from this statistic is that cloud isn’t coming – it’s very much here. Ultimately, it’s an unavoidable reality of business today,” Malan said. He was referencing a study that also highlighted how cloud adoption has soared in SA since 2013.
South Africa’s potential for technology-driven economic growth hasn’t gone unnoticed. The local interest in cloud computing has drawn several multinationals to our shores. Last month, Amazon Web Services announced its plan to open data centres in SA by 2020. Huawei recently confirmed that it will build a cloud facility in Johannesburg. And Microsoft’s sustained commitment to cloud computing in SA has already culminated in two Africa Hyperscale Cloud Data Centres (in Cape Town and Johannesburg) that are expected to come online before year end.
If you’ve been considering cloud migration, now is a good time to weigh your options. South Africa’s cloud market becomes more diverse and more competitive with each new service provider that enters it. As a business owner in the current cloud climate, you’re spoilt for choice. Plus, three of the most frequently cited reasons for cloud migration are compelling business arguments: cost efficiency, performance, and security.
Cost efficiency is a popular motivator for migrating on-premises data centres to the cloud. Maintaining on-site IT infrastructure can be a considerable expense, given the need for physical space, electrical power, cooling systems, hardware, networking and operating systems, as well as skilled staff. By shifting these responsibilities to cloud service providers (CSPs), businesses can trim their own costs and pay for cloud resources as required, or as consumed.
Substantial funds are necessary to set up an on-site data centre, and any business that makes such a commitment is then bound by a particular generation of technology. In a world where performance and agility are essential for corporate growth, such rigidity can be an obstacle. CSPs offer a variety of software platforms, processing systems, and managed databases that can be scaled in line with business needs.
CSPs across the world are subject to strict security standards enforced by governments, financial regulators, industry watchdogs, and oversight groups. CSPs are entrusted with customer data, and thus employ high-grade digital defence mechanisms. We know that computing systems can be prime targets for cybercriminals, but cloud-based security means that authentication is built in; event logging is continuous; and threat detection is possible in real time.
If you’ve made cloud adoption part of your business strategy, then it’s important to understand that a comprehensive plan of action for your cloud journey is critical.
There are four key steps to follow when migrating on-premises servers and applications to the cloud. We’ll be outlining them for you in the next four blog articles, starting with Step 1: The Readiness Assessment next week. Don’t miss a single post! Follow us on Facebook and Twitter for updates.
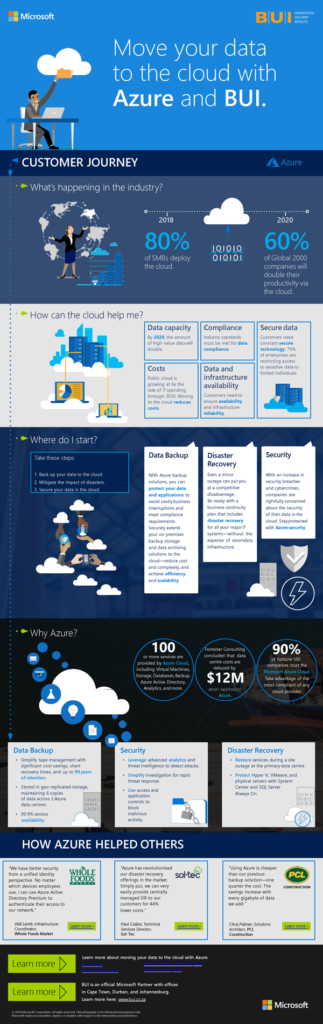
Check out the infographic below to see how extending your on-premises backup storage and data-archiving solutions to the cloud will help you achieve efficiency, scalability, and improved operational performance for your business…
Have you ever noticed what happens when you mention the cloud during a conversation? The volume tends to rise. Because the technology has passionate supporters. And fierce critics. Cloud computing has evolved rapidly in the past decade, but there’s a lot of misinformation in the public domain. Here, we tackle three prevailing myths about the cloud.
The reality… Cloud computing continues to evolve from a concept to transform the way computing resources are managed to a proven solution that delivers benefits for businesses of all sizes, according to the Information Systems Audit and Control Association (ISACA).
ISACA’s own study with the Cloud Security Alliance (CSA) found that cloud computing is no longer an emerging technology, but it’s not yet a fully mature technology, either. Cloud computing is still in the growth stage, with significant adoption and innovation across global markets.
In South Africa, cloud adoption has soared since 2013. More than 80% of the companies surveyed this year plan to increase their cloud spending. And some forecasts suggest that worldwide public cloud revenue will grow 17% in 2019. Microsoft’s recent earnings report revealed its notable success in the cloud market, and the company continues to invest in research and development initiatives to further cloud technology in every sphere of business.
Cloud-based computational power is being harnessed to address human challenges like food production and healthcare provision. Corporate decision-makers are leveraging the cloud to develop new business models and improve customer relationships. And advancements in artificial intelligence, machine learning, and the Internet of Things are being enabled by the intelligent cloud. In its infancy, cloud computing was a much-hyped phenomenon. But now, we’re seeing real opportunities for creativity, productivity, and innovation with this technology.
The reality… Cloud providers have to function according to the laws of the regions in which they operate. There are often industry-specific standards of practice or compliance regulations to adhere to as well. Physical security measures – like perimeter fences and CCTV cameras – are necessary to protect brick-and-mortar sites. And cyber security measures – like firewalls – are necessary to protect digital environments. Responsible cloud providers make every effort to ensure that the cloud is meticulously updated and constantly monitored. Do your on-premises servers receive the same care?
On-site servers require regular maintenance to perform at their peak. If a technician fails to carry out a recommended update, forgets to install a security patch, or misconfigures a firewall, then the organisation’s overall cybersecurity could be at risk.
Recent headline-making data breaches have shown us the importance of user access control and real-time threat detection. The cloud’s substantial array of cyber security tools makes it possible for technical teams to conduct continuous surveillance of machines and networks – and to respond immediately if a problem is found.
The reality… Anything that is worth doing is worth doing well. You’ve heard that idiom before, right? Successful cloud migration depends as much on the planning as it does on the execution. And, we have to admit, there’s always a lot of planning involved!
From readiness assessments and architecture evaluations, to compliance requirements and security conditions, cloud specialists have to examine organisational culture, systemic anatomy, and technical design in order to understand the migration parameters. It’s an intensive, step-by-step process designed to cover all necessary ground – but it’s not difficult. Comprehensive? Yes. Rigorous? Indeed. Detailed? Absolutely.
But when you have an experienced team to address your concerns and guide your journey, the actual process of cloud migration is relatively simple, with minimal disruption to your organisation. We’ve found that the recipe for success is a combination of expertise and strategic preparation. Click here to read more about the all-in-one Azure cloud solution we implemented for a leading financial services company. And watch this video trilogy to see how the cloud can help your business:
As cloud experts, we’re huge fans of the technology! We use it here at BUI. We deploy it for our customers. We’re excited about its broad applications for the business world. But we also know that choosing a cloud solution for your enterprise is a big decision. If you’ve got questions, we’re here to answer them. Get in touch with our team today.
Do you think our grandparents imagined anything like the supercharged laptops, tablets and smartphones available now? Do you think our mothers and fathers believed Artificial Intelligence would become a reality? The computing power we have today is truly astonishing.
Microsoft CEO Satya Nadella summarised the status quo after the company’s 2018 Build conference in Seattle: “Computing is not just an interface that you go to, but it’s instead embedded everywhere – in places, things, our homes and cities.”
Embedded. That’s the key takeaway from Nadella’s statement. We live in a world of ambient technology. Smart machines and web-enabled devices help us to communicate, connect, and carry out our daily tasks. And intelligent cloud computing has made it possible for companies of all shapes and sizes to expand their capabilities in sectors as diverse as engineering and health. What are they doing? And how are they doing it? Let’s take a closer look.
Cree, a manufacturing company specialising in silicon carbide products, needed a storage solution that could scale with the business. During a major expansion period, Cree’s IT teams turned to Azure Data Box Edge (a product from the Microsoft Azure Data Box family). Watch the video to see how cloud-based data storage gave Cree the ability to grow.
LEONI, a supplier of cables, wires, and optical fibres, developed LEONiQ – a cable system with built-in sensors and electronics to detect issues locally, so that cables can be replaced before they break. The LEONI technicians used Microsoft Azure Sphere to make their hardware perform better, and to address data security concerns. Here’s why…
Healthcare technology firm Siemens Healthineers turned to cloud computing to improve the quality of insights gained from healthcare data. Developers created a digital ecosystem using Microsoft Azure and Azure Kubernetes Services to help healthcare providers deliver more value to millions of patients. This is what they did…
Technology is changing at a rapid pace, and modern organisations have to adapt just as quickly to keep up. There’s a wide variety of intelligent cloud computing resources designed to enhance security, improve performance, and streamline processes. What would your business look like with cloud power at its core?
Microsoft CEO Satya Nadella discussed the company’s vision for the era of the intelligent cloud and the intelligent edge at the 2017 and 2018 Microsoft Build conferences in Seattle.
In both keynote speeches, he highlighted the fact that we’re living in a world powered by digital technology. And not just living in it, but participating in it, with the help of web-enabled devices that connect us in ways we often take for granted.
Nadella said the world is now, essentially, one huge computer. And he wasn’t wrong: Gartner’s research predicts that there’ll be 20 billion connected devices across the globe by 2020. Earth’s current population is around 7.4 billion. We’re definitely looking at a future with more machines than people. But what does that mean for human beings?
Opportunity, according to the Microsoft chief. The chance to take advantage of a diverse, digitally connected ecosystem. The chance to bring together industry players. The chance to create and deliver solutions that weren’t possible before. A window for change, and growth, and innovation. A time to leverage Artificial Intelligence, the Internet of Things, and Big Data to address the problems we face today, as well as the challenges we expect in the future.
Nadella calls himself an unrepentant tech optimist, and at both Build conferences he was confident about the continued evolution of cloud computing – especially as a vehicle for delivering products and services to customers. Microsoft aims to harness advancements in machine learning to give people the tools they need to accomplish more in less time. How? By capitalising on the processing power of the intelligent cloud, and the data-gathering power of devices at the intelligent edge.
Microsoft defines the intelligent cloud as “ubiquitous computing, enabled by the public cloud and artificial intelligence technology, for every type of intelligent application and system you can envision”.
If you take a closer look at the definition, you’ll see that Microsoft is talking about the everyday, everywhere kind of computing that we tend to dismiss. But don’t forget that computers themselves are no longer the big, clunky machines of yesteryear. Today, computers can fit inside the smartwatch on your wrist and the mobile phone in your pocket. Technological development, combined with industrial-scale production, has seen an explosion of small, powerful, and cost-effective computational devices that are web-enabled or directly connected to the cloud.
Nadella has also said that, simply put, the intelligent cloud refers to Microsoft’s ongoing drive to build AI into all of its applications and services, to ensure that customers’ data is always with them (and constantly available) no matter which device they use.
“Our homes, our cars, our workplaces, our factories and cities – every sector of our economy, whether it’s precision agriculture, precision medicine, autonomous cars or autonomous drones, personalised medicine or personalised banking – are all being transformed by digital technology,” Nadella wrote on LinkedIn after the 2018 Build event. “As computing becomes woven in to the fabric of our lives, the opportunities are endless.”
“The intelligent edge is a continually expanding set of connected systems and devices that gather and analyse data – close to users, the data, or both. Users get real-time insights and experiences, delivered by highly responsive and contextually aware apps,” according to Microsoft.
Plainly speaking, the “edge” in intelligent edge is a reference to the devices that are close to where they need to be (in order to function purposefully), but are still connected to the cloud. Consider, for example, an agricultural research drone… It’s a physical device designed to operate in a specific location, but its accumulated data can be transferred via the cloud to farmers on the ground, to facilitate immediate decision-making. The drone’s on-board sensors can gauge environmental factors like wind speed, so the device has “intelligence” to enable it to “understand” and adapt to its surroundings.
“When we take the power of the cloud down to the device – the edge – we provide the ability to respond, reason, and act in real time,” explained Kevin Scott (Executive Vice President and Chief Technology Officer, Microsoft) in a recent blog post. “With the power of AI enabling these devices to intelligently respond to the world they are sensing, we will see new breakthroughs in critical areas that benefit humanity, like healthcare, conservation, sustainability, accessibility, and disaster recovery.”
Microsoft believes the intelligent cloud will inspire intuitive new apps and services that give organisations and businesses the insights they need to achieve greater productivity and efficiency. As cloud specialists ourselves, we’re keen to see what the next wave brings.
BUI has won the Microsoft Cloud Platform Partner of the Year accolade at Microsoft South Africa’s 2018 Partner Awards.
Well done, team!
The gala presentation was held on October 9, 2018, in Johannesburg.
BUI was also named as a finalist in the Hybrid Cloud Partner of the Year and Modern Workplace Partner of the Year categories.
The awards ceremony is held annually to acknowledge Microsoft partners that have excelled in delivering Microsoft solutions. Judging takes place across numerous competencies, and is based on criteria including innovation, customer acquisition, social responsibility commitments, and more.
Managing Director Ryan Roseveare was thrilled to receive the Microsoft Cloud Platform Partner of the Year trophy.
“This is a repeat win for BUI. It’s also the award everyone wants to win,” he said. This victory marks BUI’s fourth consecutive achievement in this cloud-centric category.
Roseveare congratulated the whole BUI team. “We grew our already large Azure base by 300% and performed several world-first Azure services migrations,” he said.
Cloud adoption continues to gain traction in South Africa, and the imminent launch of Microsoft’s hyperscale cloud data centres in Cape Town and Johannesburg is also driving interest in the technology.
BUI is proud to be recognised for its premier abilities in cloud.
How are you protecting your sensitive data and personal information? Your cybersecurity could be at risk if you’re not implementing these fundamental precautions in your daily digital life…
Obvious, right? We know. But life is hectic. It’s easy to forget a software renewal or security update when you’re busy at work or caught up in the daily realities of family life.
Having up-to-date security software, a modern operating system, and the latest version of your favourite web browser will strengthen your overall defence against cyber threats like viruses and malware.
How often do you connect to the Internet? And how do you do it? Tablet? Mobile phone? Smartwatch? Gaming console?
The computer on your desk is not the only machine that needs protection from online dangers. Think about the smaller devices on your wrist, in your hand, or in your pocket. They need to be shielded from cybercriminals, too.
External hard drives, flash drives, and other plug-and-play peripherals are susceptible to the same malicious infections that could jeopardise your computer.
Stop and think before you connect a new device to your machine. Do you know what’s on that USB stick? Do you trust the person who gave it to you? Even if you do, run a security scan anyway.
Usernames and passwords aren’t enough to protect important assets like your email and online banking accounts. Opt for the strongest authentication tools available to you: iris scans, fingerprint scans, and one-time codes will add extra layers of security to your logins.
In the absence of multi-factor authentication, make sure you create powerful passwords unique to each account. Include a mix of alphanumeric and special characters, and use uppercase and lowercase letters. Do not rely on easy-to-guess passwords like 12345678 and QWERTY. Ever.
When you’re banking or shopping online, check that the website is secure. Look for the https:// in the URL so that you know your connection to the website is encrypted.
Some web browsers provide visual cues about website safety… For example, a padlock icon in the URL field to indicate a secure website. Verify that protective measures are in place before you enter sensitive personal or financial information.
No technology is impervious to cybercriminals, but you can improve your personal cybersecurity by being more responsible online, today and every day.
And they’re duty-bound to ensure the privacy and security of such sensitive material.
But it’s not always easy in digital environments with multiple end-users and multiple points of access.
That’s why we’ve created Legalty.
Legalty gives lawyers, attorneys, partners, paralegals, and their support staff the tools they need to work securely – and efficiently – everywhere, every day.
How?
By combining the law firm’s existing legal software and Microsoft 365 in a managed, cloud-based environment that supports data encryption and device control. With built-in security. With built-in redundancy protocols. With comprehensive technical support. With a transparent pricing plan. Without bulky hardware. And without costly local servers.
Legalty can be deployed for legal practitioners using LegalSuite, Lexis Convey, and most other third-party legal software applications.
Our all-in-one solution helps law firms to:
Legalty includes Office 365, with perennially popular Microsoft applications (like Excel, Word, and PowerPoint) that are up to date and accessible anywhere, at any time, using a computer, tablet, smartphone, or other device connected to the Internet.
Legalty comes with top-notch communication tools that enable group email, team chat, and collaborative online meetings, as well as calendaring and scheduling facilities to simplify diary planning and management.
Legalty also features Advanced Threat Protection, a comprehensive security solution designed to protect organisations from increasingly sophisticated phishing and ransomware attacks.
Want to know how Legalty can help your law firm to achieve more? Explore the Legalty website.
Keen to see Legalty in action? Request a demo with our team.