Zandre Janse van Vuuren explains why cybercrime spikes during the holiday season and shares practical tips to help you protect your organisation from opportunistic attackers.
By Zandre Janse van Vuuren | Service Delivery Manager: Cyber DFIR, BUI
The months of November and December are a perfect storm for cybercriminals. Retailers, logistics companies, and organisations closing out their financial year are at peak operational intensity, processing high volumes of sales, payments, and customer data.
But just as business activity surges, security staffing drops. Key personnel take annual leave, incident response teams shrink, and IT capacity thins out. This imbalance creates what’s known as the “holiday blackout”, a seasonal window when attackers know defences are down and reaction times are slow.
During this period, cybercriminals ramp up their ransomware, phishing and extortion campaigns to strike when you’re least prepared. And their goal isn’t just to breach your defences: it’s to disrupt your operations when downtime is most damaging.
The solution? In a word: readiness. By focusing on cyber resilience (your ability to protect your critical assets, respond to inevitable attacks, and recover quickly), you can keep your business running and reduce the risk of financial and reputational damage when attackers do strike.
The holiday season threat landscape
The holiday season brings an uptick in cybercrimes and digital scams that exploit distraction, emotion, and urgency. Understanding this threat landscape is essential for developing a proactive security strategy for your organisation.
1 | The phishing epidemic
Phishing is consistently identified as the number one social engineering strategy. During the holiday season, cybercriminals know that people are juggling personal shopping, shipping alerts and end-of-year workplace tasks, which lowers vigilance and increases click rates. Common phishing campaigns include:
- Shipping scams, where cybercriminals impersonate retailers, couriers, or postal agencies – often through text messages or emails that include fake tracking information and compromised links.
- Financial or account fraud, including payment confirmations for items the user never purchased or notifications claiming the user’s account is locked, disabled, or requires immediate login verification.
- Fake invoices and payroll alerts disguised as internal communications, where specific social engineering lures (such as fake “payroll date change” or “payroll alert” messages) are deployed to steal the user credentials necessary for organisational system access.
- Charity and job scams designed to prey on people’s emotions at a time when NGOs and charities appeal for generosity and jobseekers and recruiters are focused on seasonal employment opportunities.
When inboxes and screens are flooded with legitimate notifications, a fake one can slip through easily – especially when employees are too stressed or too distracted to stop and interrogate a suspicious message.
2 | Access brokers and ransomware
Behind many of these phishing campaigns are access brokers who specialise in gaining unauthorised initial access to organisational networks and then selling that access to ransomware groups. There’s typically a surge in access-broker activity at the end of the year when networks are busy, oversight is reduced, and employees are overwhelmed with tasks at home and at work. Successful breaches often become the entry point for larger ransomware attacks that unfold over the holidays.

Table: Threat vectors that organisations must prepare for during the holiday season
3 | The security staffing gap problem
The biggest enabler of seasonal cybercrime is reduced security staffing. Attackers time their strikes for weekends, public holidays and vacation periods, knowing that organisations are at their most vulnerable. Industry research highlights the risk clearly:
- Four out of 10 organisations reduce their security staffing by up to 70% during weekends and holidays.
- About 21% operate with only a skeleton crew, cutting staff by as much as 90%.
Meanwhile, modern cyberattacks move quickly: it often takes less than an hour from the moment a user clicks on a malicious link until the attacker establishes a firm foothold in the system. When critical security personnel are unavailable, alerts may go unread for hours or even days, giving attackers free rein. The risk isn’t just slower detection; it’s complete operational paralysis until normal staffing resumes. That’s why seasonal security planning should prioritise rapid response capability, not just detection.
Building cyber resilience: What really works
Cyber resilience requires more than robust technical defences and safeguards: it demands a strategic mindset. At the very least, you should:
1 | Be aware of the dangers
Don’t ever think you’re too small to be targeted. It’s a myth that cybercriminals ignore startups and micro- and medium-sized businesses. Smaller organisations like these are prime targets precisely because they likely have fewer defences. Remember, cybercrime has been industrialised: attackers sell stolen credentials and exploitative tools on the dark web, enabling virtually anyone to target any company’s digital assets.
2 | Patch and protect your systems
Legacy or unpatched systems can be easy entry points for cybercriminals – and once they’re in, they can take advantage of existing vulnerabilities, flaws, and weaknesses in your environment. If you’ve neglected your systems and become lax about your security, then a single breach could snowball into a catastrophic business failure. Make sure you concentrate on patching and protecting your systems before key security staff go on vacation.
3 | Review your identity and access management policies
Robust identity and access management controls and device encryption are essential throughout the year – but even more so during the holiday season when security teams are smaller and more pressured. Make sure you enforce strong password policies and encrypt all sensitive data (at rest and in transit) to help prevent data leaks in the event that business devices are mishandled, lost, or stolen.
4 | Have a comprehensive (and tested) incident response plan
A written incident response plan isn’t good enough; it needs to be tried and tested. Many organisations still haven’t rehearsed what to do if a ransomware attack occurs over a weekend or holiday period. Make sure you’ve run tabletop exercises, tested communications and capabilities under low-staff conditions, and confirmed that everyone knows their role.
5 | Train and empower your people
Human error remains the top cause of breaches. Take the time to give your employees a refresher course in password hygiene, general security awareness and vigilance, and the correct technical route for raising and reporting issues. Regular mini training sessions that address the current threat landscape (for example, a 10-minute overview of seasonal phishing tactics) can be more effective than lengthy presentations.
Cyber resilience means having a framework that protects your key assets, enables an effective response, supports quick recovery, and maintains customer trust even after a successful cyberattack. Building this framework involves assessing risks, keeping hardware and software updated, reviewing access policies, and enforcing security standards across your connected environment.
The yearend cyber resilience checklist: 12 essential steps
A phased, actionable checklist is necessary to translate strategic goals into measurable operational tasks. This checklist outlines the actions with the highest impact, organised by deployment priority, leading up to the end-of-year shutdown.
Phase 1: Pre-holiday system hardening (T-30 days)
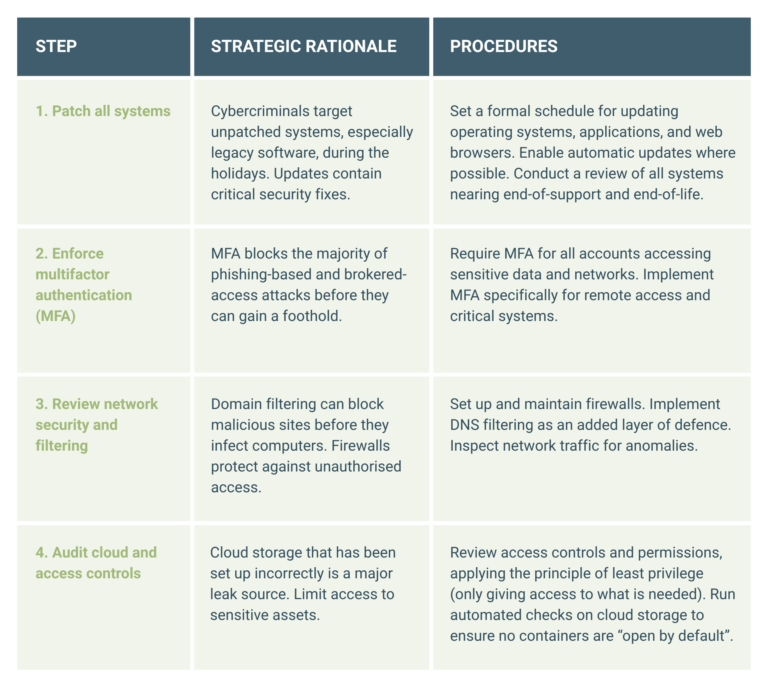
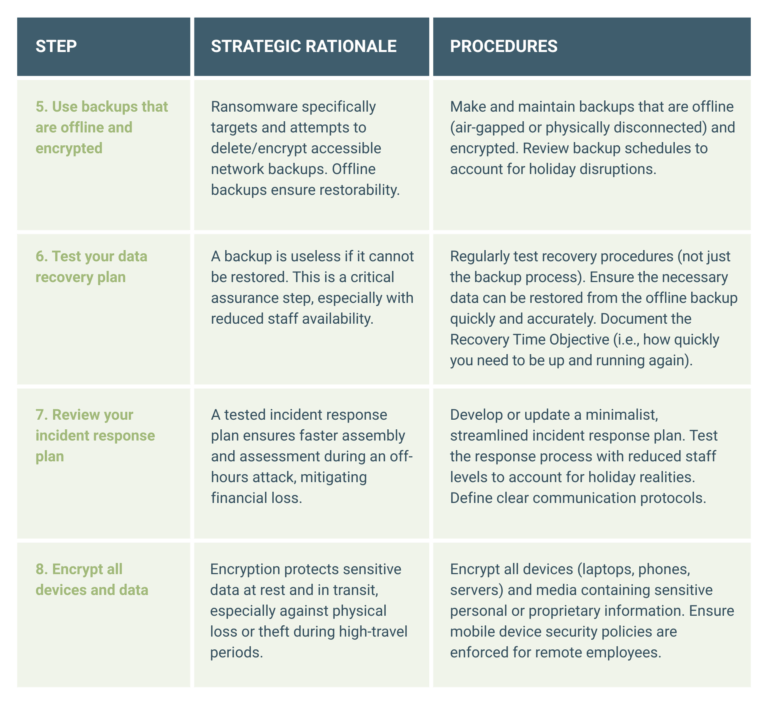
Phase 2: Data protection and recovery assurance (T-14 Days)
Data-recovery capabilities are paramount over the holiday season because a cyberattack during low staffing risks permanent data loss. Your focus must be on assuring restorability rather than merely assuming backups exist.
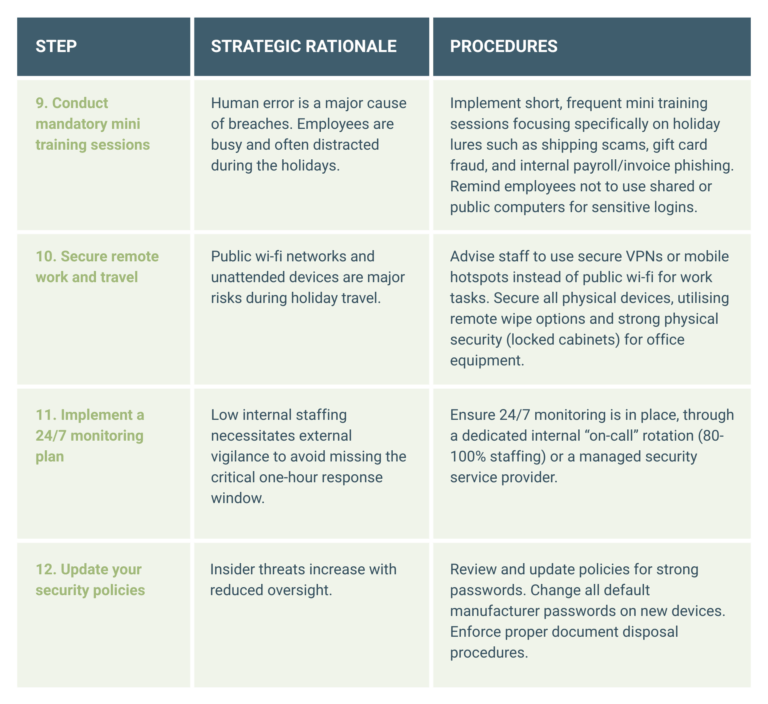
Phase 3: Make your staff your first line of defence (T-7 Days)
The final week should be focused on staff education so that your people are aware of the heightened risk landscape and the prevalence of seasonal scams.
The weeks leading up to the holidays present one of the most dangerous periods of the year for cyberattacks. Well-organised threat groups know that yearend pressures, reduced staffing, and increased digital activity create ideal conditions to strike.
Preventing every attack isn’t realistic, but ensuring your business can withstand, respond to, and recover from one absolutely is. True cyber resilience means being ready for disruption, but this resilience isn’t built overnight: it’s achieved through deliberate preparation, tested plans, and continuous learning.
As the festive season approaches, take the opportunity to validate your defences. Run your incident response plan under reduced staffing conditions. Test your offline backups. Confirm that your recovery strategy actually works when key personnel are away.
The threats of the holiday period are predictable – and that makes them preventable. By being proactive now, you can protect your systems, your data, and your business reputation to ensure a smooth start to the new year.
Cyber threats evolve constantly and your security strategy has to keep up. If you want expert guidance, improved detection capabilities, or help building operational resilience, reach out to our security team and we’ll guide you forward. Get started today.
